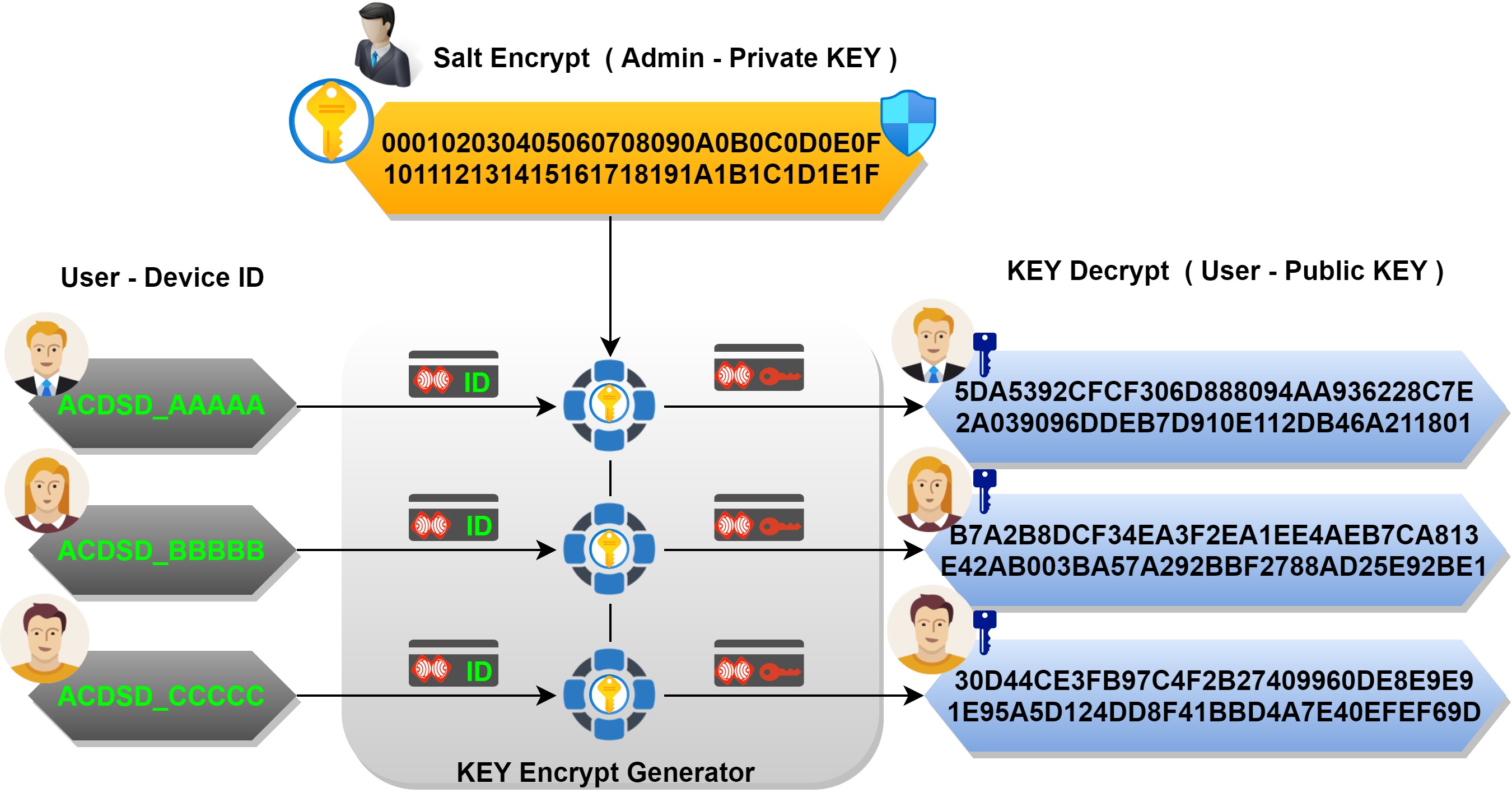
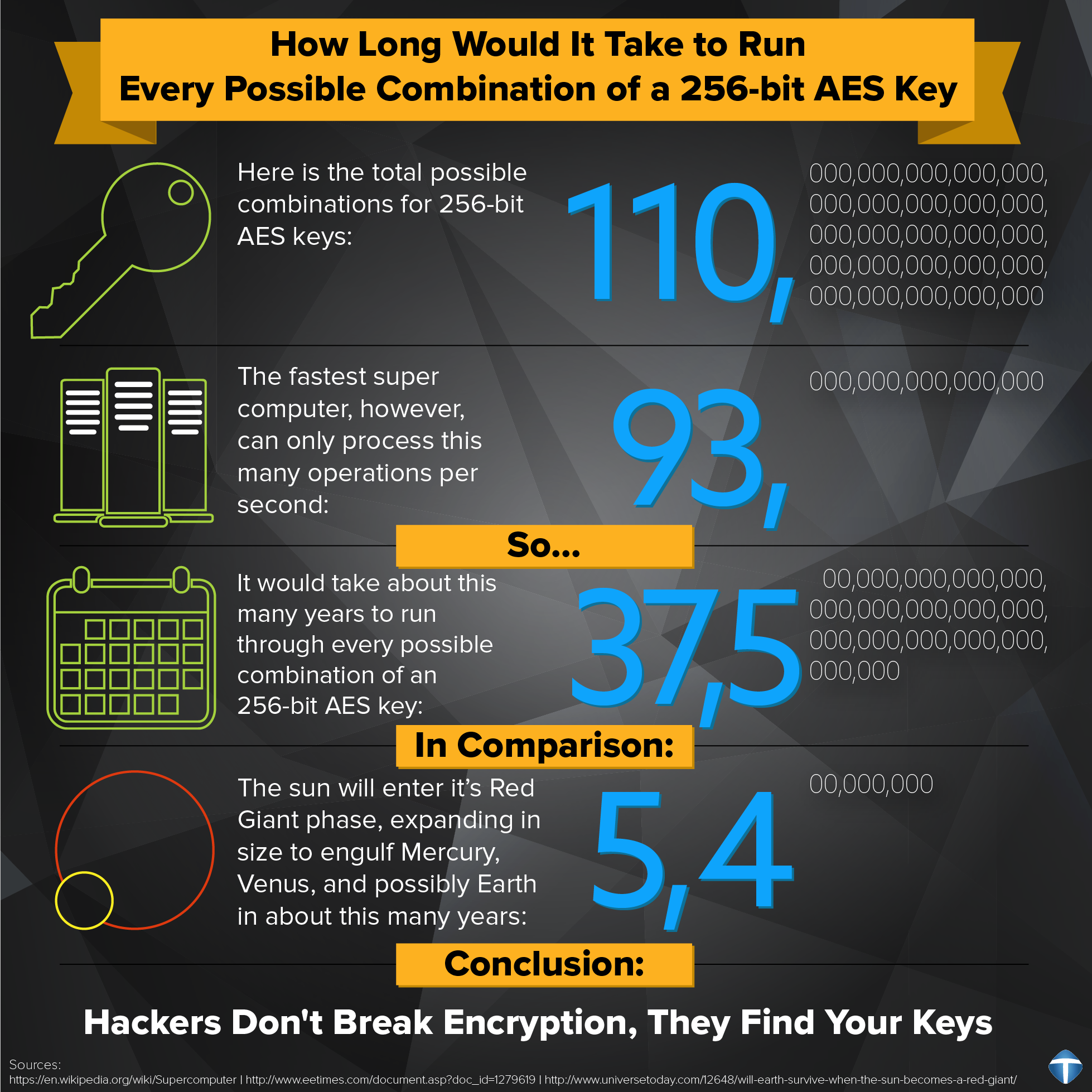
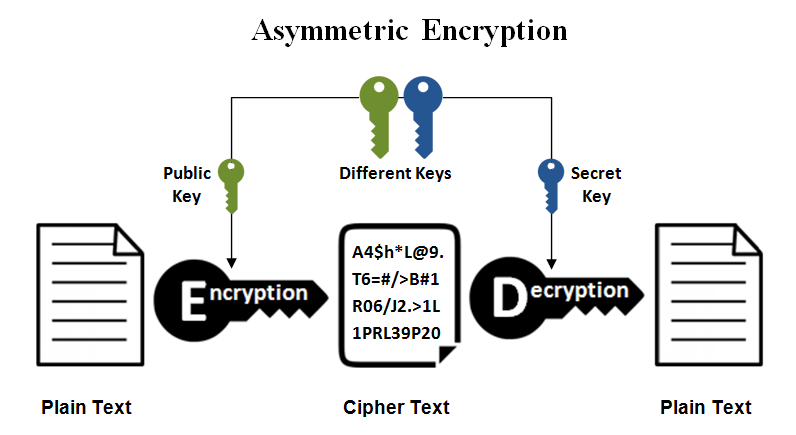
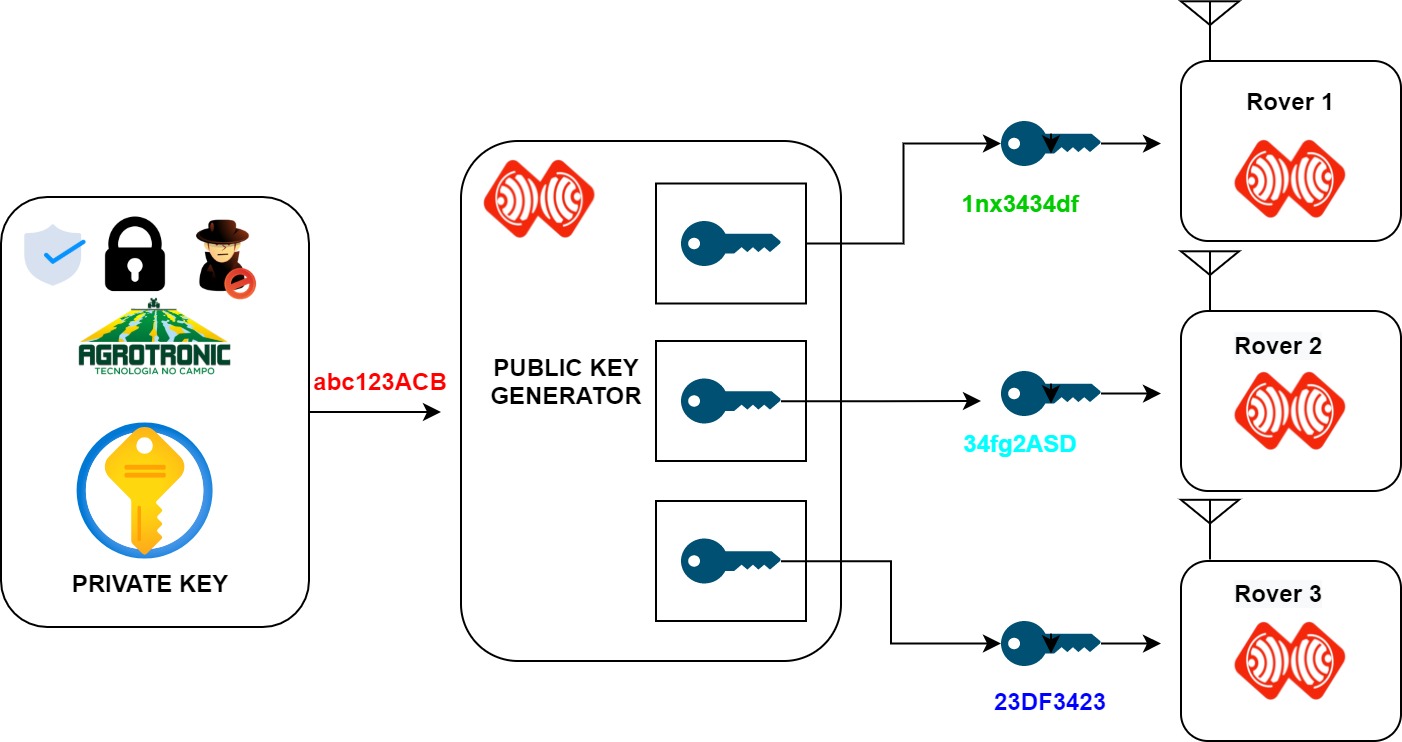
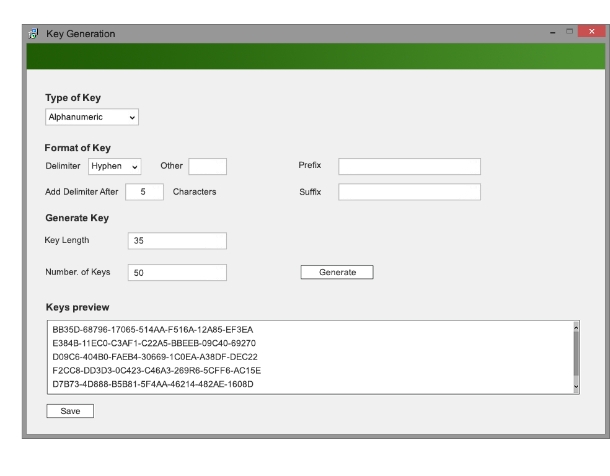
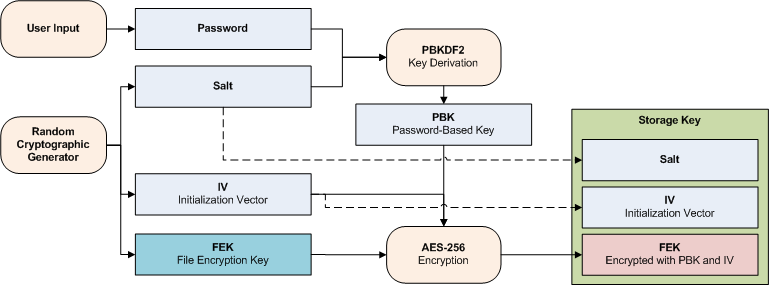
Enhanced key-generation algorithm using MRMCTT in Data encryption standard algorithm | Semantic Scholar

Security aspects of removing a user from an organization or collection - Vaultwarden Forum (formerly Bitwarden_RS)
Online RSA Key Generator,Encryption and Decryption web application-Spring Boot web application free download

Generation of Cryptographic Keys from Personal Biometrics: An Illustration Based on Fingerprints | IntechOpen
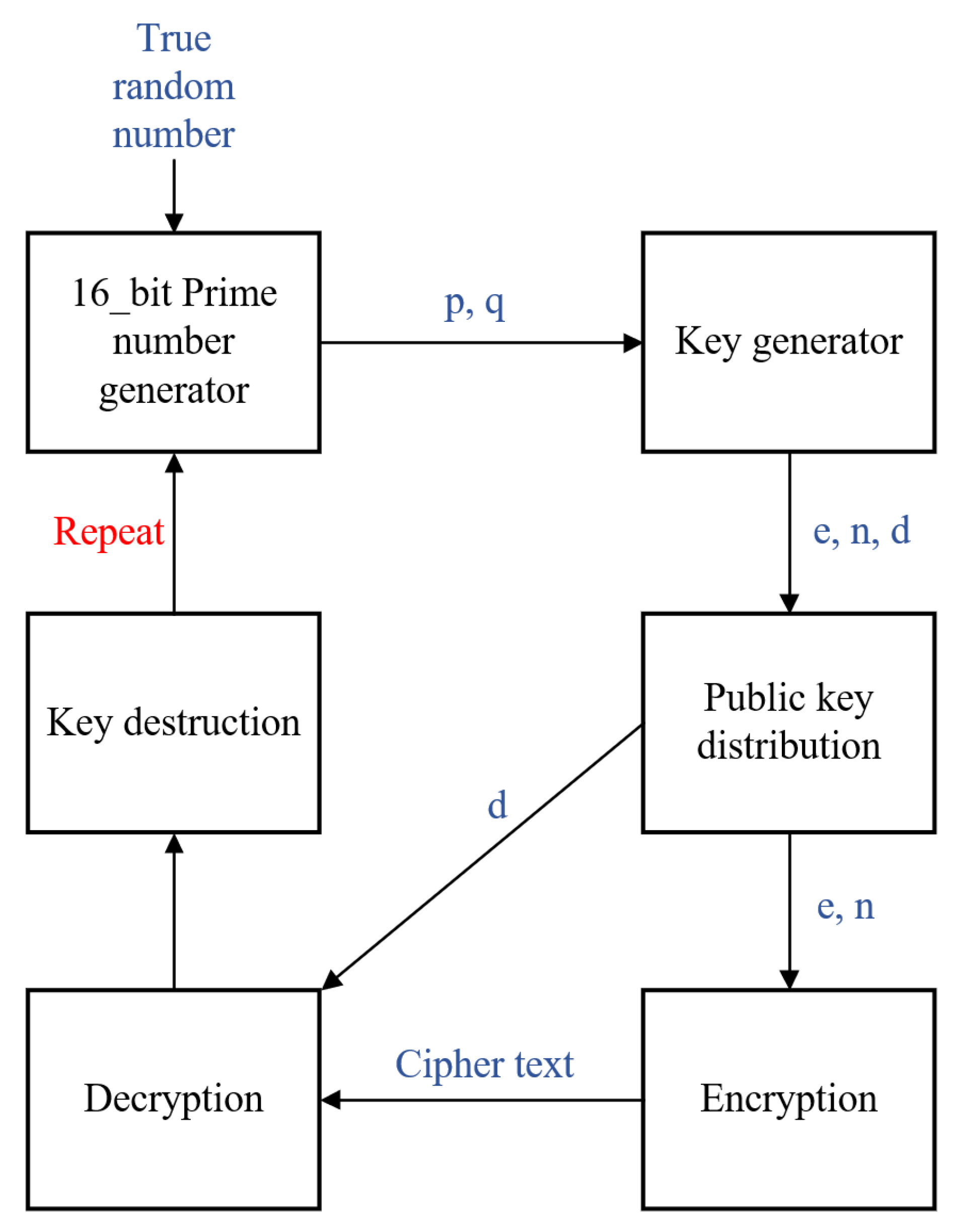
Electronics | Free Full-Text | New RSA Encryption Mechanism Using One-Time Encryption Keys and Unpredictable Bio-Signal for Wireless Communication Devices
File:KG-83 Key Generator Encryption-Decryption Equipment - National Cryptologic Museum - DSC08014.JPG - Wikimedia Commons

CJMCU 608 Cryptographic Key Storage Random Number Generator Signature Encryption Decryption Module|encryption keys| - AliExpress